We recommend that all NiTO users enable Two Factor Authentication (2FA). 2FA can be activated on a per-user basis under the user’s config; “Name & Credentials” section at https://portal.nito.net. SMS and TOTP (Time-based One-time Password) methods are available, with TOTP being the recommended method combined with a 3rd-party authenticator app (e.g., Duo or Google Authenticator).
A user can enable/disable 2FA only for themselves, and Top-Level Admin users within the same account can disable 2FA for another user (i.e., in case a user loses access to the device they were using for 2FA, to temporarily disable 2FA so that the user can login with just username/password and re-enable 2FA).
TOTP
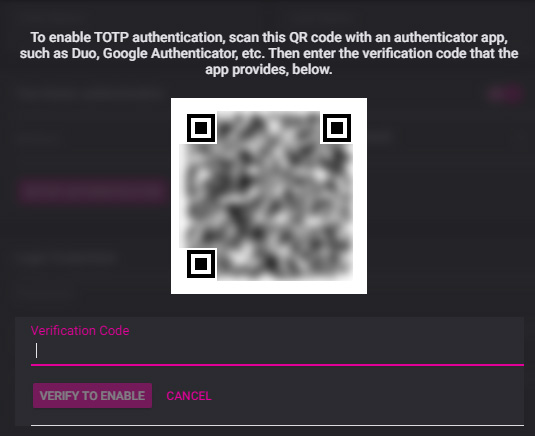
The user for which 2FA is being enabled must be logged-in to NiTO and prepared with an authenticator app on a separate device (i.e., their smartphone). Upon toggling-on 2FA, NiTO will present a unique QR code to be scanned by the user’s authenticator app. The authenticator app will then provide a verification code to finalize the activation of 2FA.
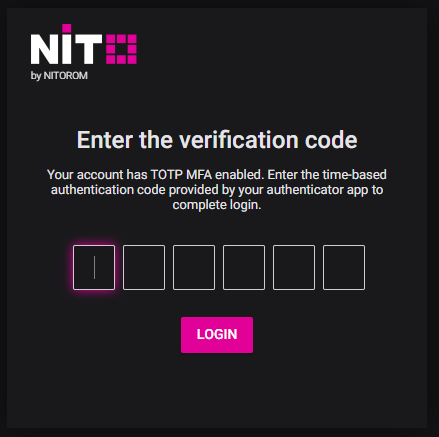
From now on, whenever the user logs-in to NiTO, they will be prompted with an additional step to enter the temporary 6-digit code provided by their authenticator app.
SMS
Although TOTP is the recommended method offered by NiTO for 2FA, we also offer SMS-based 2FA for rare situations where TOTP may not be possible for a user. Note that with SMS 2FA, there is a greater chance of your authentication code being intercepted outside the NiTO network (i.e., over your cellphone provider’s network). Enabling SMS 2FA is similar to TOTP, however, an authenticator app is not required and instead you will be SMS’ed a verification code whenever you attempt to login to NiTO.